
Keysight BreakingPoint
BreakingPoint
All-in-one applications and network security testing platform
BreakingPoint recreates every aspect of a realistic network including scale and content to validate the security posture of your network.

Real-World Applications + Performance
-
490+ applications & 4000+ user scenarios to create your unique representative traffic profiles
-
100’s of predefined profiles based on internal ATI research, partnerships, and third-party research
-
Load profiles to model the dynamic nature of traffic
-
Ultra-high performance with mixed application traffic profiles
Simulates both clients and servers, enabling users to:

Pre-Deployment Technology Validation
-
Make rapid decisions about competing products & technologies with data-driven PoCs
-
Right-size your investment with scale and capacity testing
Continuous Integration

-
Verify that network upgrades and software patches don’t degrade application performance
-
Validate the QoE of new application rollouts and its impact on existing services
-
Accelerate NFV/SDDC deployments

Training & Optimization
-
Optimize security posture by understanding the impact of changes to security policies
-
Train your people and improve cyber resiliency and readiness
Keysight’s Cyber Range solution
-
Provides a controlled environment for security professionals to gain hands-on cyber skills and to test the organization’s security posture.
Practice
TRAIN YOUR CYBER WARRIORS WITH ADVANCED CYBER RANGE SERVICES


Network Visibility
REAL-TIME, END-TO-END DYNAMIC NETWORK INTELLIGENCE FOR PHYSICAL, VIRTUAL, SDN AND NFV NETWORKS
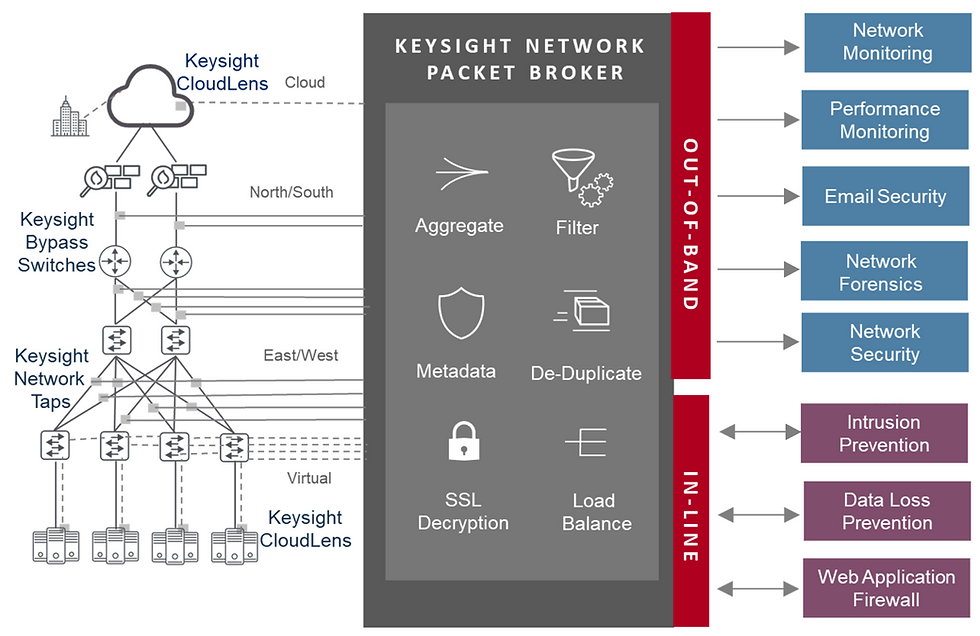
Passive Network Visibility: Out of Band Monitoring
High-performance data access and distribution

Network Tapping & Packet Brokering

Industry Leading
PERFORMANCE
-
4X faster NPB
-
FPGA accelerator
-
No dropped packets
CONCURRENT FEATURES
-
One NPB, no complex cabling
-
Simultaneous features
PERFORMANCE
-
Drag-and-drop
-
No coding
-
Auto validates connections
PERFORMANCE
-
External bypass
-
High availability
-
Fast failover
CloudLens
END-TO-END VISIBILITY ACROSS YOUR CLOUD ENVIRONMENTS - PUBLIC, PRIVATE, AND HYBRID CLOUDS
Visibility Platform for Public, Private and Hybrid Cloud

PRIVATE CLOUD
ESXi, NSX, KVM, Hyper-V, Azure Stack, Containers
HYBRID CLOUD
PUBLIC CLOUD
AWS, Azure, GCP, IBM
CAPTURE ALL RELEVANT DATA
INTELLIGENT FILTERING - DPI - METADATA GENERATION
Improve Your Network Security and Monitoring Insights With Keysight
When companies like yours rely on network connectivity and performance, having accurate information about what happens within your company is critical. You need to know which parts of your network are working well and where problems might occur. At Keysight Technologies, they offer the best solutions for your professional networking security and monitoring needs.



